Every few months, the internet becomes obsessed with a strange code. This time, it’s lna2u9h2f1k7.
At first glance, it looks like a password. Or a software key. Or maybe a hidden cheat code. But the real question is simple:
What does lna2u9h2f1k7 actually mean?
Is it a file hash?
A database identifier?
A viral hoax?
Or just random characters that caught attention?
In this complete guide, we’ll break it down in plain English. No fluff. No exaggeration. Just facts, logic, and analysis.
What Is lna2u9h2f1k7?
The term lna2u9h2f1k7 is an alphanumeric string made up of:
-
11 total characters
-
Lowercase letters
-
Numbers
-
No special symbols
It doesn’t form a recognizable word. It doesn’t follow standard formatting rules like license keys. And it doesn’t match common cryptographic hash lengths. That’s why people are confused.
In simple terms:
lna2u9h2f1k7 appears to be a random string with no officially documented meaning.
But let’s go deeper.
Why Did lna2u9h2f1k7 Go Viral?
People love mysteries. When a random code appears online without explanation, curiosity spreads fast. This has happened before with puzzles like Cicada 3301, which turned random-looking symbols into global investigations. The same psychology applies here.
Reasons this string gained attention:
-
It looks technical.
-
It resembles a hash or secret key.
-
It has no official explanation.
-
Blogs began speculating.
-
SEO pages amplified it.
Mystery + internet = viral speculation.
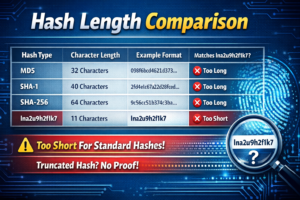
Is lna2u9h2f1k7 a File Hash?
One of the strongest theories is that lna2u9h2f1k7 is a file hash. Let’s test that idea.
What Is a File Hash?
A file hash is a digital fingerprint created using cryptographic algorithms such as:
-
MD5
-
SHA-1
-
SHA-256
These algorithms are standardized by institutions like the National Institute of Standards and Technology. Hashes verify file integrity. If a single character changes in a file, the hash changes completely.
Could lna2u9h2f1k7 Be a Software Identifier?
This is more plausible.
Modern software generates random strings for:
-
Session IDs
-
Authentication tokens
-
Temporary file names
-
Debug placeholders
-
Database keys
Developers often use short random strings during testing.
An 11-character identifier is reasonable for:
-
Internal testing
-
Logging systems
-
Temporary API responses
But again, there is no official documentation linking this string to any real software.
API Tokens and Digital Communication
When systems talk to each other, they exchange identifiers. APIs (Application Programming Interfaces) rely on tokens to verify sessions and users. Security frameworks recommended by organizations like OWASP stress the importance of unpredictable tokens. Could lna2u9h2f1k7 be one? Possibly.
But real API tokens are usually longer and include:
-
Uppercase letters
-
Special characters
-
Longer sequences
This one is relatively simple.
Gaming Theory: Is lna2u9h2f1k7 a Cheat Code?
Gamers frequently search for secret codes. Classic examples include the Konami Code. Gaming unlock codes often look random. So the theory isn’t unreasonable.
However:
-
No game developer has confirmed it.
-
No official patch notes mention it.
-
No verified gameplay footage proves it works.
Most mentions appear on speculation-based blogs. So the gaming theory remains weak.
Is lna2u9h2f1k7 an SEO Experiment?
Now we enter interesting territory. Some website owners target completely random keywords because:
-
No competition exists.
-
Ranking is easy.
-
It generates curiosity traffic.
-
It boosts indexing signals.
Publishing articles about mystery strings is a known tactic. If that’s the case, then lna2u9h2f1k7 may simply be a fabricated keyword used to attract traffic. This theory is actually strong.
Technical Pattern Analysis of lna2u9h2f1k7
Let’s examine its structure.
-
11 characters
-
Alternating pattern: letters and numbers
-
Lowercase only
-
No repeating sequence patterns
This suggests it could be:
-
Auto-generated
-
Randomized using a simple algorithm
-
Produced by a pseudo-random generator
Entropy and Randomness
Entropy measures unpredictability.
If each character has:
-
26 lowercase letters
-
10 digits
That’s 36 possible characters per position. Possible combinations: 36¹¹ ≈ 131 trillion possibilities
That’s a large space.
Meaning: It’s statistically easy to generate random strings like this.
So randomness alone does not make it meaningful.
Could It Be Malware Related?
Whenever unknown strings appear, people worry. Security professionals often check suspicious hashes using services like VirusTotal.
But remember:
A string alone is harmless.
It becomes dangerous only if:
-
Attached to malicious software
-
Used in phishing links
-
Part of suspicious downloads
There is no verified malware connection.
Real-World Codes That Look Similar
Let’s compare with legitimate examples.
1. Software License Keys
Example: XXXXX-XXXXX-XXXXX-XXXXX
These follow specific formats.
2. Blockchain Hashes
Used in cryptocurrencies like Bitcoin.
These are extremely long, structured hashes.
3. Session Identifiers
Often 16–64 characters long.
Compared to these, lna2u9h2f1k7 is minimal and simple.
Psychological Fascination With Mystery Codes
Why are people so drawn to this?
Three reasons:
1. Pattern Recognition Bias
Humans search for meaning in randomness.
2. Fear of Missing Out (FOMO)
What if it unlocks something important?
3. Internet Puzzle Culture
After events like Cicada 3301, people assume hidden meanings everywhere.
Mystery fuels engagement.
Pros and Cons of Leading Theories
Pros
-
Looks technical.
-
Matches identifier patterns.
-
Could be generated by software.
-
Easy to mistake for hash.
Cons
-
No official source.
-
Too short for cryptographic standards.
-
No real-world confirmation.
-
High chance of being random.
How to Safely Investigate Unknown Codes
If you encounter a string like this:
-
Do not panic.
-
Check context.
-
Use trusted tools.
-
Avoid “decode now” scam sites.
-
Scan files with reputable antivirus software.
Never enter passwords on suspicious platforms.
How Developers Generate Strings Like This
Programmers often use:
-
Random string generators
-
UUID libraries
-
Token functions
In languages like Python:
This could easily produce something like lna2u9h2f1k7.
Which strengthens the “random generation” theory.
Could AI Generate lna2u9h2f1k7?
Yes. Language models and algorithms frequently output:
-
Random sequences
-
Placeholder IDs
-
Synthetic tokens
It requires no advanced system to generate such a string.
Digital Forensics Perspective
In cybersecurity investigations:
-
Analysts classify unknown strings.
-
They check databases.
-
They look for matches.
-
They analyze length patterns.
If a string is too short and has no database match, it is typically categorized as random noise.
Is There Any Verified Origin?
As of now:
-
No official company claims it.
-
No developer documentation references it.
-
No major software lists it.
-
No confirmed game supports it.
This suggests:
There is no verified origin.
Final Technical Verdict
After analyzing:
-
Hash structure
-
Token length
-
Identifier standards
-
Security frameworks
-
Statistical probability
The most logical explanation is:
lna2u9h2f1k7 is a randomly generated alphanumeric string that gained attention through speculation and SEO amplification.
There is no confirmed deeper meaning.
Conclusion
The mystery of lna2u9h2f1k7 teaches an important lesson.
Not every code hides a secret.
Sometimes, randomness becomes popular simply because humans dislike uncertainty.
Technically speaking:
-
It’s too short to be a real hash.
-
Too undocumented to be official.
-
Too simple to be cryptographically significant.
Most evidence suggests it’s either:
-
Randomly generated
-
Used temporarily in testing
-
Or amplified for SEO curiosity
In the end, lna2u9h2f1k7 is more about internet culture than hidden technology.
And sometimes, the mystery is more powerful than the meaning.
2. Is lna2u9h2f1k7 a virus?
No. A string alone cannot infect a device.
3. Is it a file hash?
Unlikely. It’s too short to match standard cryptographic hashes.
4. Can it be decoded?
Not unless context is known.
5. Is it linked to gaming?
There is currently no verified evidence that lna2u9h2f1k7 is linked to any official video game, gaming platform, or developer. Some online discussions speculate that it could be a cheat code, unlock key, or hidden in-game identifier because it resembles the random strings often used in gaming systems. However, no reputable game publisher has confirmed its use. Until official documentation or credible sources connect it to a specific game, it should not be considered a legitimate gaming code.
6. Why are people searching for it?
People are searching for lna2u9h2f1k7 mainly due to curiosity and online speculation. When a mysterious alphanumeric string appears without explanation, it naturally attracts attention. Blogs, forums, and SEO-driven articles amplify the curiosity, which leads more users to investigate. In many cases, viral discussions and the fear of missing out (FOMO) contribute to increased searches, even when the term has no confirmed meaning.
7. Could it be an API token?
In theory, lna2u9h2f1k7 could resemble a simple API token or session identifier because such systems often use randomized alphanumeric strings. However, real-world API tokens are usually much longer and include more complex character combinations to ensure security. There is no confirmed documentation linking this specific string to any known API or authentication system. Without technical context, it remains speculative.
8. Is it dangerous?
By itself, lna2u9h2f1k7 is not dangerous. It is simply a string of characters. However, context matters. If the string appears in connection with suspicious downloads, phishing links, or unknown executable files, caution is advised. A standalone alphanumeric code cannot harm a device, but users should always evaluate where and how they encountered it before assuming it is safe.
9. Should I remove it if I see it in logs?
Not necessarily. Random-looking strings commonly appear in system logs as session IDs, temporary file names, or database identifiers. If you notice lna2u9h2f1k7 in your logs, first review the surrounding entries to understand its context. If it appears during normal application processes and there are no security alerts, it is likely harmless. Only take action if other suspicious behavior is present.
10. Could hackers use strings like this?
Hackers do use alphanumeric strings in certain activities, such as generating tokens, encryption keys, or malicious file names. However, these strings are typically much longer and more complex than 11 characters. While lna2u9h2f1k7 could theoretically resemble a randomly generated value, there is no evidence linking it to hacking activity. Length and complexity are important indicators when assessing security risks.
11. Is it connected to blockchain?
There is no evidence connecting lna2u9h2f1k7 to blockchain technology. Blockchain systems, including cryptocurrencies, use long cryptographic hashes that are significantly more complex and structured. Transaction IDs and wallet addresses are much longer and follow strict formats. This string does not match the characteristics of blockchain-related identifiers.
12. Is it part of a hidden puzzle?
Some online discussions compare mysterious codes like lna2u9h2f1k7 to famous internet puzzles. However, there is no verified indication that it is part of any organized challenge, alternate reality game, or cryptographic puzzle. Without official clues, coordinated messaging, or credible sources, the hidden puzzle theory remains purely speculative.
13. Can AI generate similar strings?
Yes, AI systems and basic random string generators can easily produce sequences similar to lna2u9h2f1k7. Even simple programming scripts can generate thousands of comparable alphanumeric combinations in seconds. The structure of this string does not require advanced algorithms or encryption, making it highly likely that it could be machine-generated.
14. Is it an SEO trick?
It is quite possible that lna2u9h2f1k7 is being used as part of an SEO experiment. Some website owners intentionally target unique or meaningless keywords to rank quickly due to low competition. By publishing content around mysterious codes, they attract curiosity-driven searches and increase traffic. While this cannot be confirmed without insider information, the SEO amplification theory is one of the more plausible explanations.
15. Why does it look technical?
Alphanumeric combinations often resemble system-generated identifiers, passwords, or cryptographic hashes. Because people frequently encounter similar patterns in software keys, database entries, and security tokens, lna2u9h2f1k7 appears technical even if it has no official meaning. The format itself triggers familiarity with digital systems.
16. Will it become important later?
There is currently no evidence suggesting that lna2u9h2f1k7 will gain official significance in the future. While internet trends can evolve unexpectedly, most random strings eventually fade from attention unless tied to a real product, service, or event. Without credible developments, it is unlikely to become historically important.
17. Is it safe to ignore?
Yes, in most cases, it is safe to ignore lna2u9h2f1k7. If you encounter it in casual browsing or search results, there is no reason for concern. However, if it appears alongside suspicious software, unknown files, or phishing attempts, further investigation may be necessary. Context always determines risk.

